TL;DR
ESET has identified “HybridPetya,” a Petya/NotPetya-style ransomware that extends into the firmware layer by planting a malicious EFI application on the EFI System Partition and abusing CVE-2024-7344 to bypass UEFI Secure Boot on outdated systems. That combination enables pre-OS persistence and faster encryption of the NTFS master file table (MFT). Organizations should prioritize firmware and Secure Boot updates, audit EFI partitions for unauthorized files, and monitor for boot-chain tampering alongside traditional ransomware controls.
What’s new
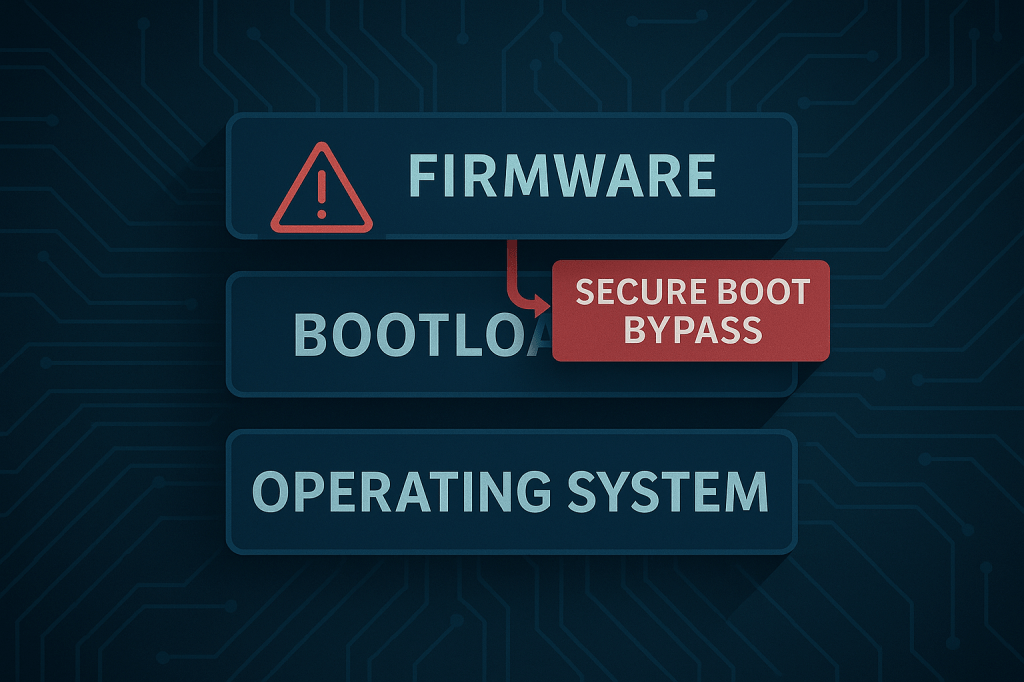
ESET’s researchers reported HybridPetya after samples surfaced in VirusTotal. Unlike the 2017 variants, this strain targets modern UEFI-based systems by dropping a malicious EFI application that runs before the operating system, then proceeds to encrypt the MFT, blocking access to file content while the system still appears to boot normally.
How the attack works
HybridPetya weaponizes CVE-2024-7344, a Secure Boot bypass first described by ESET in January 2025. On systems that haven’t implemented updated revocation lists or platform-vendor fixes, the malware can load untrusted pre-OS code. From there, it establishes persistence in the EFI partition and manipulates the boot sequence—before detonating its MFT-targeting payload to accelerate impact.
Why this is hard to catch
Firmware-level implants execute under the OS, so endpoint defenses only see the aftermath. Even when the OS is reimaged, the malicious EFI component can re-infect unless defenders explicitly clean and re-seal the boot chain. That’s why ESET’s disclosure stresses the Secure Boot bypass as the critical enabler—and why firmware telemetry and attestation should be treated as first-class signals.
Detection and hunting ideas
Focus hunts on changes to the EFI System Partition and boot configuration. Look for unexpected files or recent writes under \EFI\ folders, anomalous bootloader hashes, and any evidence that Secure Boot policy or revocation lists haven’t been updated. Tie this to ransomware behavior on the OS side—sudden MFT access anomalies and fake “disk check” messages are classic Petya-family tells, echoed in recent ecosystem write-ups.
Mitigation guidance
Start with platform hygiene: update UEFI firmware, apply Secure Boot DB/DBX revocations from your OEM, and validate that CVE-2024-7344 mitigations are in place. Expand monitoring to include boot-chain integrity (firmware/bootloader measurements), and add controlled boot-time attestation where feasible. On Windows fleets, pair these changes with strong credential hygiene, application control, and resilient backups tested for bare-metal recovery—because firmware-enabled ransomware undercuts “reimage-and-move-on” playbooks.
References
- ESET WeLiveSecurity — “Introducing HybridPetya: Petya/NotPetya copycat with UEFI Secure Boot bypass” (Sept. 12, 2025).
- ESET newsroom/press summary — HybridPetya details (UEFI implant, MFT encryption).
- ESET WeLiveSecurity — “Under the cloak of UEFI Secure Boot: Introducing CVE-2024-7344” (Jan. 16, 2025).
- Eclypsium analysis note on HybridPetya and firmware lessons.

Leave a comment