Author: RedSecNinja
-
Microsoft’s New Security Store Brings Agentic AI to the SOC—Promise, Pitfalls, and Procurement
Microsoft’s Security Store brings Security Copilot agents to Defender/Sentinel/Entra/Purview—what it means and how to govern safely.
-

Supply-Chain Risk in AI Agent Tooling: Malicious MCP Server on npm
TL/DR:On September 2025, security researchers discovered the first malicious Model Context Protocol (MCP) server in the wild. A fake npm package called postmark‑mcp—marketed as an official Postmark integration—inserted a one‑line backdoor starting in version 1.0.16 that quietly blind‑copies every email sent by an AI agent to the attacker’s domain (giftshop[.]club) [1]. Because MCP servers run…
-

Akira Ransomware Is Rocketing Through SonicWall SSL VPNs (Even with MFA)
TL/DR:Since late July 2025, Akira affiliates have ramped up intrusions via SonicWall SSL VPN logins, often bypassing OTP-based MFA—likely using stolen OTP seeds. Dwell time can be under one hour from VPN login to ransomware deployment. Patch CVE-2024-40766, reset VPN credentials, revoke/replace OTP seeds, and enforce network segmentation with per‑app MFA (not just VPN). Monitor…
-

CISA ED 25-03: Cisco ASA Exploited—What Orgs Must Do Now
TL;DR On September 25, 2025, CISA issued Emergency Directive ED 25-03 requiring federal agencies to find and mitigate compromises of Cisco Secure Firewall ASA and Firepower devices, citing active exploitation of CVE-2025-20333 (RCE) and CVE-2025-20362 (auth bypass). These CVEs are now in the KEV catalog. A separate—but concurrent—zero-day (CVE-2025-20352) affects Cisco IOS/IOS XE’s SNMP subsystem…
-
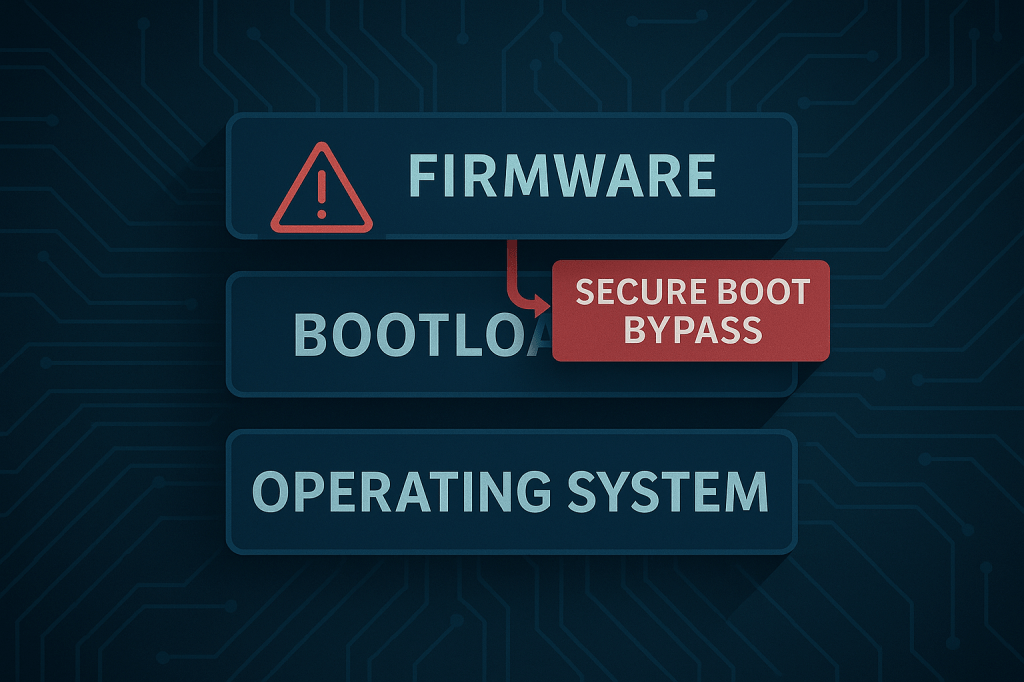
HybridPetya: UEFI Bootkit + Ransomware, Explained
TL;DR ESET has identified “HybridPetya,” a Petya/NotPetya-style ransomware that extends into the firmware layer by planting a malicious EFI application on the EFI System Partition and abusing CVE-2024-7344 to bypass UEFI Secure Boot on outdated systems. That combination enables pre-OS persistence and faster encryption of the NTFS master file table (MFT). Organizations should prioritize firmware…
-

Webshells in Well-Known Paths: A Stealthy Persistence Vector
**TL;DR** Attackers are actively probing `/.well-known/` on public websites and, in some cases, planting webshells there to gain durable access that blends into routine traffic. SANS Internet Storm Center honeypots recorded a surge of requests for PHP files under `/.well-known/`—including the `acme-challenge/` and `pki-validation/` subfolders—on September 25, 2025, and highlighted why adversaries like this location:…
-

Subtle Snail Hits Telcos & Satellite Operators with Job-Lure Phishing
Introduction Iran-aligned Charming Kitten has launched a focused campaign against telecommunications providers, satellite operators, aerospace firms and defense organizations. Security researchers track the cluster as Subtle Snail or UNC1549 and report that the attackers used LinkedIn-style job lures to deliver custom loaders such as MINIBIKE and MINIBUS while hiding command and control traffic behind popular…
-
Turla x Gamaredon: First Documented Collaboration Targets High-Value Machines in Ukraine
Introduction Russian state-linked threat actors Turla (also known as Snake) and Gamaredon appear to be teaming up in Ukraine, blending Gamaredon’s noisy initial access techniques with Turla’s precision espionage tooling. Researchers at ESET recently observed four machines that were compromised by both groups this year. They even saw Gamaredon implants being used to restart Turla’s…
-
Secure Boot Under Siege: How Signed Drivers Enable BYOVD Attacks
In September 2025, researchers at Binarly released a comprehensive study that challenges the assumption that Secure Boot is impervious to tampering. Secure Boot depends on a chain of trust anchored by signed modules, but Binarly’s team found that a large number of legitimately signed UEFI drivers and shells contain vulnerabilities that can be weaponized to…
