Author: RedSecNinja
-

CastleRAT Unveiled: Inside TAG 150’s Multifaceted Malware Operation
Researchers reported in early September 2025 that the malware-as-a-service group TAG 150 has strengthened its CastleLoader campaign with a pair of new CastleRAT variants. According to a news brief, these trojans enable system data exfiltration, remote command execution and delivery of additional payloads. The more advanced CastleRAT variant is written in C and expands the scope…
-
Single Account, Massive Risk: Unpacking the npm Supply‑Chain Crypto Clipper Attack
In early September 2025, attackers compromised a widely used npm account belonging to a well‑known developer. By sending a convincing phishing email impersonating npm support, they stole the maintainer’s credentials and pushed malicious updates to eighteen popular packages like chalk, strip‑ansi and color‑convert. These packages collectively saw billions of downloads each week. The rogue updates…
-
Chatbots Under Siege: Unraveling the Salesloft Drift Supply-Chain Breach
The incident underscores how a single compromised integration can cascade across hundreds of organizations. To prevent similar attacks, companies should inventory third-party vendors, enforce least‑privilege for API tokens, and monitor logs for suspicious queries. Vendors, meanwhile, must maintain rigorous code‑repository security and disclose breaches promptly to limit downstream exposure. In early 2025, the Salesloft integration…
-

How Amazon Foiled a Stealthy APT29 Credential Theft Campaign
Threat actors leveraged Cloudflare Workers and Microsoft’s device-code authentication to execute a covert credential theft campaign. Amazon disrupted the operation by blocking malicious domains and device-code flows. Learn about the attack chain and how to defend against similar threats.
-

ScarCruft Uses RokRAT Malware in Operation HanKook Phantom Targeting South Korean Academics
Researchers from Seqrite Labs discovered Operation HanKook Phantom spear‑phishing campaign using ScarCruft’s RokRAT malware to target academics and government officials. Learn how the attacks work and how to defend against them.
-
When Browsers Become the Attack Surface: Rethinking Security for Scattered Spider
As enterprises shift to SaaS and web apps, browsers have become a primary attack surface. Scattered Spider’s browser-focused tactics use BitB overlays, session token theft and malicious extensions. Learn how these attacks work and how to protect your organisation.
-
Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling
Threat actors misused the open source Velociraptor incident‑response tool and the Visual Studio Code editor to create a covert command‑and‑control tunnel in a recent attack. Learn how the attackers abused legitimate tools and what organisations can do to detect and defend against this novel abuse.
-

Google will verify all Android developers in four countries to combat malicious apps
Google announced that all Android developers in Brazil, Indonesia, Singapore and Thailand must verify their identity by 2026. This new requirement aims to prevent malicious actors from quickly distributing new apps after takedowns. Learn about the timeline and what it means for developers and users.
-

ShadowCaptcha campaign hijacks WordPress sites to deliver ransomware, info‑stealers and cryptominers
The ShadowCaptcha campaign uses compromised WordPress sites to redirect visitors to fake CAPTCHA pages that install information stealers, Epsilon Red ransomware and cryptocurrency miners. Learn how the attack works and how to defend your organization.
-
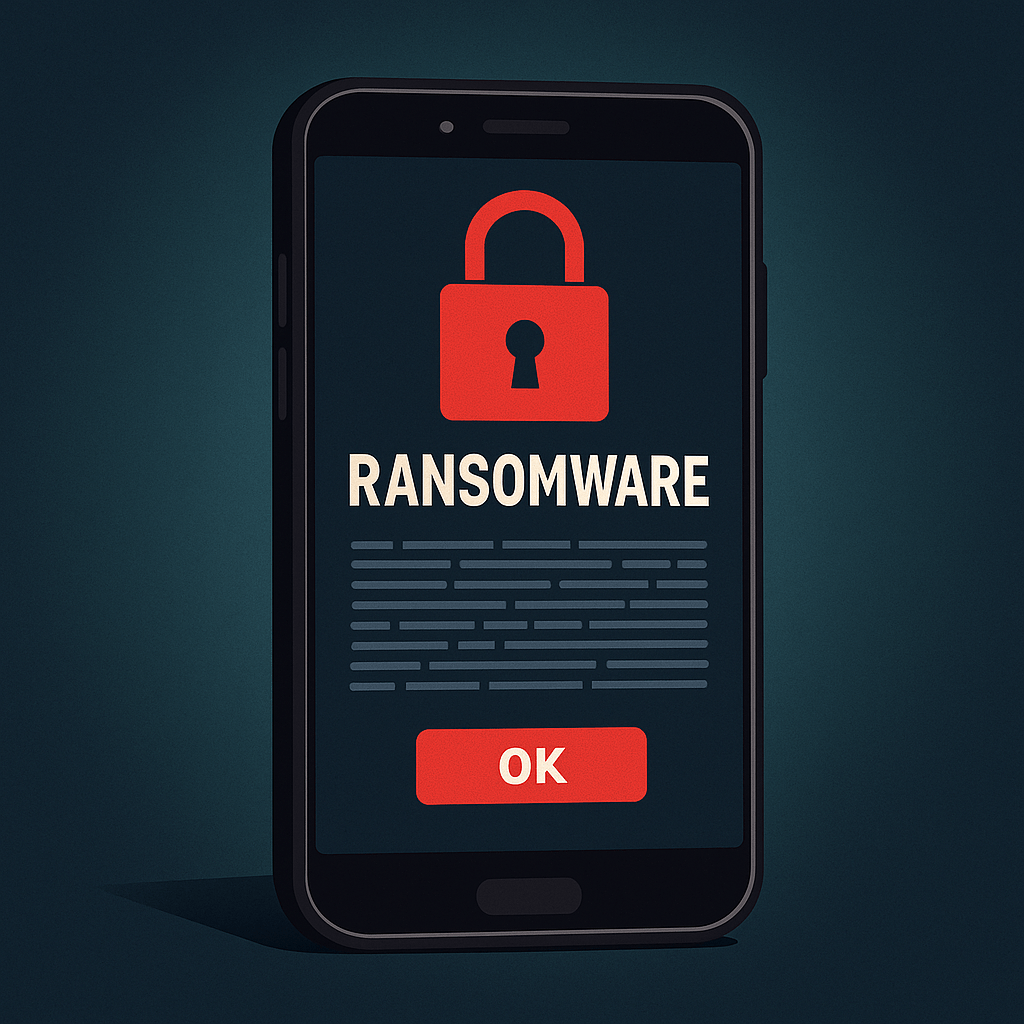
HOOK Android Trojan adds ransomware overlays and over 100 commands
A new variant of the HOOK Android banking trojan adds a full-screen ransomware overlay triggered by remote commands and expands its arsenal to 107 commands, enabling credential theft, fake overlays and device takeover. Learn about this threat and how to protect yourself.
