Category: Cybersecurity
-
Microsoft’s New Security Store Brings Agentic AI to the SOC—Promise, Pitfalls, and Procurement
Microsoft’s Security Store brings Security Copilot agents to Defender/Sentinel/Entra/Purview—what it means and how to govern safely.
-
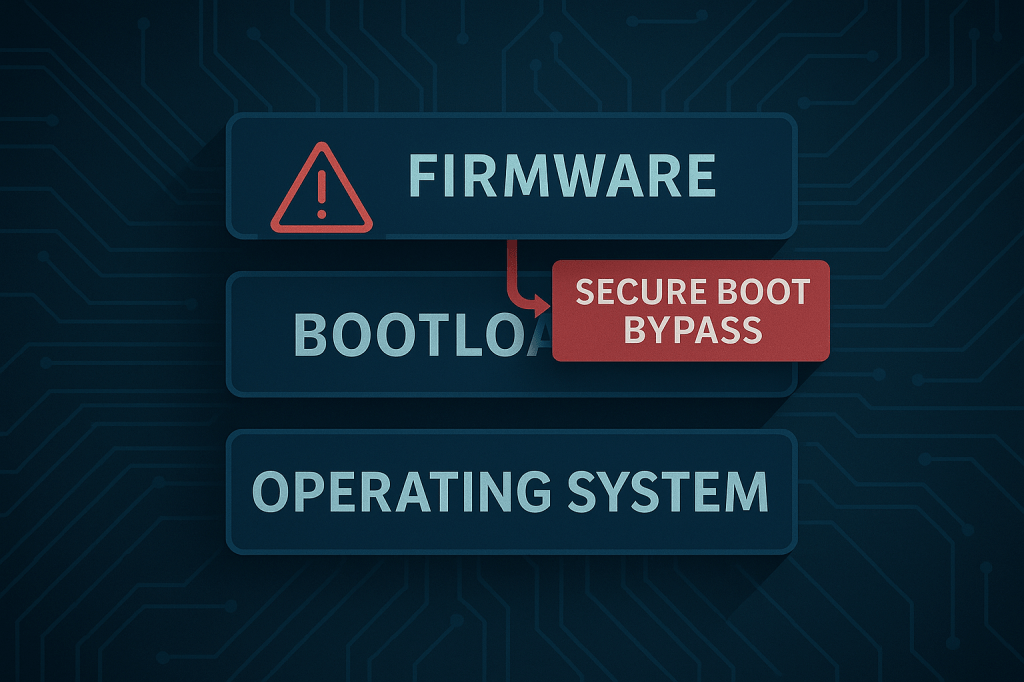
HybridPetya: UEFI Bootkit + Ransomware, Explained
TL;DR ESET has identified “HybridPetya,” a Petya/NotPetya-style ransomware that extends into the firmware layer by planting a malicious EFI application on the EFI System Partition and abusing CVE-2024-7344 to bypass UEFI Secure Boot on outdated systems. That combination enables pre-OS persistence and faster encryption of the NTFS master file table (MFT). Organizations should prioritize firmware…
-

Webshells in Well-Known Paths: A Stealthy Persistence Vector
**TL;DR** Attackers are actively probing `/.well-known/` on public websites and, in some cases, planting webshells there to gain durable access that blends into routine traffic. SANS Internet Storm Center honeypots recorded a surge of requests for PHP files under `/.well-known/`—including the `acme-challenge/` and `pki-validation/` subfolders—on September 25, 2025, and highlighted why adversaries like this location:…
-

Subtle Snail Hits Telcos & Satellite Operators with Job-Lure Phishing
Introduction Iran-aligned Charming Kitten has launched a focused campaign against telecommunications providers, satellite operators, aerospace firms and defense organizations. Security researchers track the cluster as Subtle Snail or UNC1549 and report that the attackers used LinkedIn-style job lures to deliver custom loaders such as MINIBIKE and MINIBUS while hiding command and control traffic behind popular…
-
Secure Boot Under Siege: How Signed Drivers Enable BYOVD Attacks
In September 2025, researchers at Binarly released a comprehensive study that challenges the assumption that Secure Boot is impervious to tampering. Secure Boot depends on a chain of trust anchored by signed modules, but Binarly’s team found that a large number of legitimately signed UEFI drivers and shells contain vulnerabilities that can be weaponized to…
-

CastleRAT Unveiled: Inside TAG 150’s Multifaceted Malware Operation
Researchers reported in early September 2025 that the malware-as-a-service group TAG 150 has strengthened its CastleLoader campaign with a pair of new CastleRAT variants. According to a news brief, these trojans enable system data exfiltration, remote command execution and delivery of additional payloads. The more advanced CastleRAT variant is written in C and expands the scope…
-
Single Account, Massive Risk: Unpacking the npm Supply‑Chain Crypto Clipper Attack
In early September 2025, attackers compromised a widely used npm account belonging to a well‑known developer. By sending a convincing phishing email impersonating npm support, they stole the maintainer’s credentials and pushed malicious updates to eighteen popular packages like chalk, strip‑ansi and color‑convert. These packages collectively saw billions of downloads each week. The rogue updates…
-
Chatbots Under Siege: Unraveling the Salesloft Drift Supply-Chain Breach
The incident underscores how a single compromised integration can cascade across hundreds of organizations. To prevent similar attacks, companies should inventory third-party vendors, enforce least‑privilege for API tokens, and monitor logs for suspicious queries. Vendors, meanwhile, must maintain rigorous code‑repository security and disclose breaches promptly to limit downstream exposure. In early 2025, the Salesloft integration…
-

How Amazon Foiled a Stealthy APT29 Credential Theft Campaign
Threat actors leveraged Cloudflare Workers and Microsoft’s device-code authentication to execute a covert credential theft campaign. Amazon disrupted the operation by blocking malicious domains and device-code flows. Learn about the attack chain and how to defend against similar threats.
