Tag: incident response
-
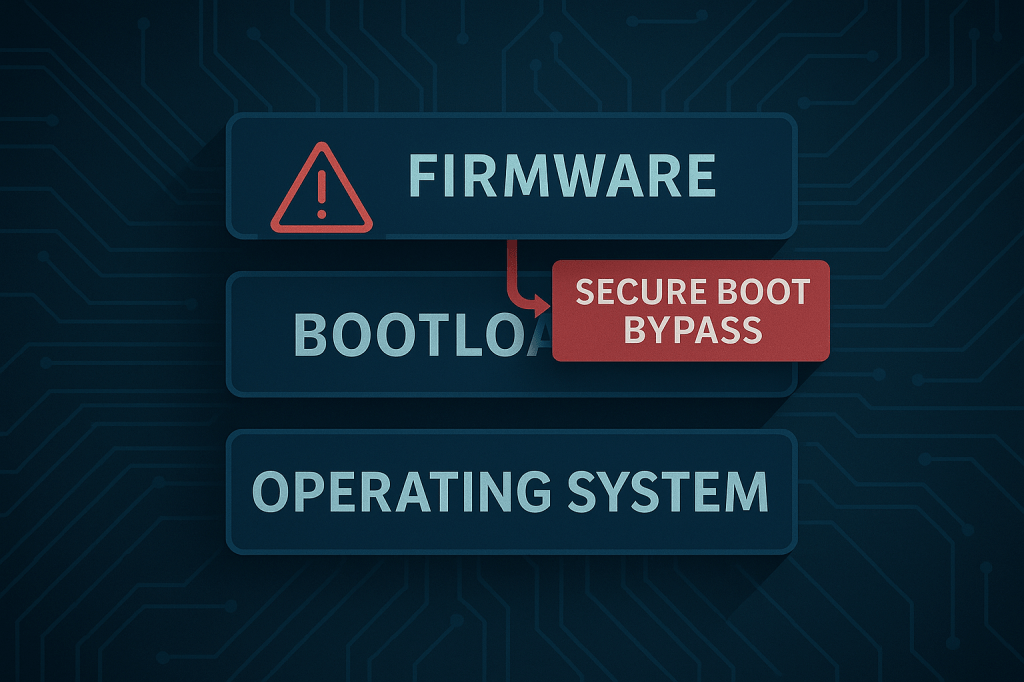
HybridPetya: UEFI Bootkit + Ransomware, Explained
TL;DR ESET has identified “HybridPetya,” a Petya/NotPetya-style ransomware that extends into the firmware layer by planting a malicious EFI application on the EFI System Partition and abusing CVE-2024-7344 to bypass UEFI Secure Boot on outdated systems. That combination enables pre-OS persistence and faster encryption of the NTFS master file table (MFT). Organizations should prioritize firmware…
-

Webshells in Well-Known Paths: A Stealthy Persistence Vector
**TL;DR** Attackers are actively probing `/.well-known/` on public websites and, in some cases, planting webshells there to gain durable access that blends into routine traffic. SANS Internet Storm Center honeypots recorded a surge of requests for PHP files under `/.well-known/`—including the `acme-challenge/` and `pki-validation/` subfolders—on September 25, 2025, and highlighted why adversaries like this location:…
-
Attackers Abuse Velociraptor Forensic Tool to Deploy Visual Studio Code for C2 Tunneling
Threat actors misused the open source Velociraptor incident‑response tool and the Visual Studio Code editor to create a covert command‑and‑control tunnel in a recent attack. Learn how the attackers abused legitimate tools and what organisations can do to detect and defend against this novel abuse.
